The Value of OneFirewall
During the PoV, you will see how cyber actors hitting your infrastructure and if they are currently being prevented.
Leveraging the intrusion detection work of 180+ Security Centers for your own protection. Without the cost of running one.
What you will get
Current Firewall & IPS Cyber Efficiency Report:
(1) A PDF Summary with findings and Crime Score
(2) A CSV file listing all detected attacks not blocked
(3) Cost Saving Potentials
Start a Proof of Value
Once you submit this form, our team will contact you to schedule a session to kick off the Proof of Value (PoV) on your infrastructure.
Proof of Value
Demonstrate OneFirewall's efficacy in identifying and mitigating cyber threats within your infrastructure
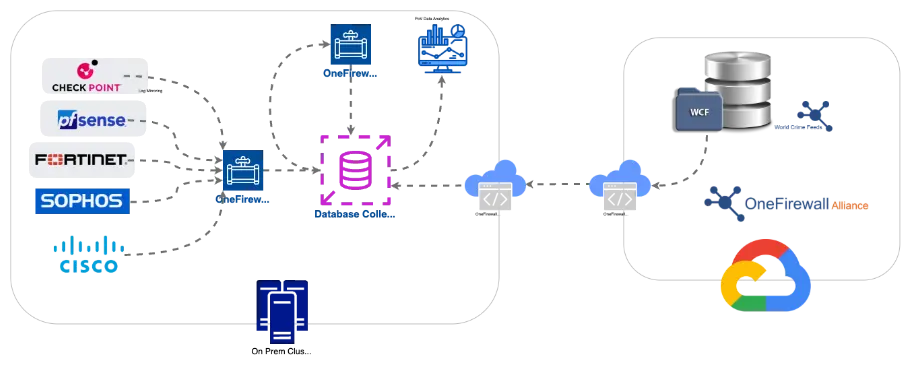
The Proof of Value (PoV)aims to demonstrate the efficacy of OneFirewall in identifying and mitigating potential cyber threats within an on-premises environment, including private cloud infrastructures. This is achieved by installing a Virtual Machine running the OneFirewall platform and analyzing edge traffic logs to detect malicious activities.
Understanding the Value
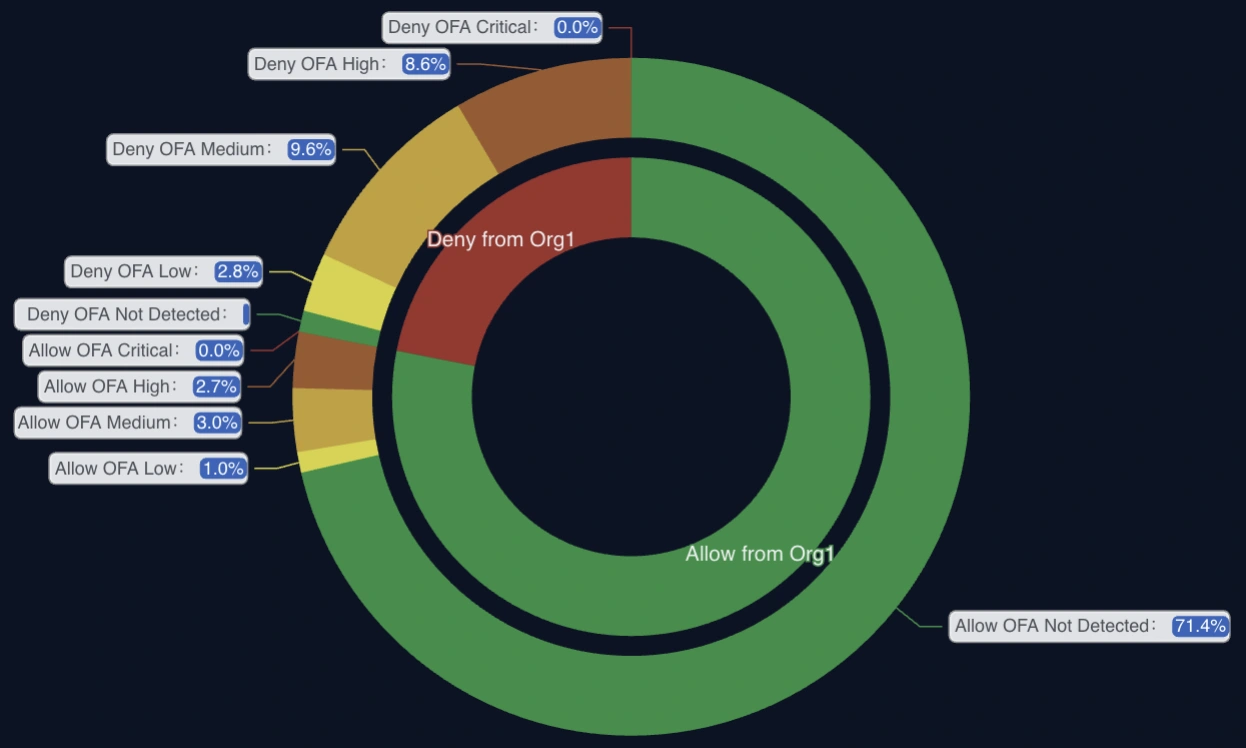
What you will see in real time: malicious connection attempts, scanning activity, brute force attacks, exploitation attempts, suspicious outbound connections, and repeat attacker infrastructure already classified across the Alliance.
The results shows you the attacks you are exposed to that are not being blocked — and how collective intelligence changes the outcome.
Real-Time Threat Detection
Identifies malicious actors attempting to penetrate your network perimeter before damage occurs
Comprehensive Visibility
Analyzes edge traffic to provide complete insight into potential security threats
Actionable Intelligence
Delivers real-time alerts and detailed reports on detected threats, enabling rapid response
Risk-Free Evaluation
Deploy in your environment to assess effectiveness without long-term commitment
By participating in the PoV, organizations can gain firsthand experience with OneFirewall's capabilities, evaluate its performance in their specific environment, and make informed decisions about integrating it into their cybersecurity strategy.
The PoV Process
Preparation
- Prepare a Linux-based virtual machine (Ubuntu, Debian, Red Hat, or equivalent) with Docker and Docker Compose installed
- Ensure the selected on-premises environment or private cloud instance meets all network and permission requirements needed for deployment
- Provide the required access credentials (VPN, VM credentials with sudoers rights) to the OneFirewall team, who will handle the setup and configuration
Installation
- The OneFirewall OnPrem Solution—a fully containerized ecosystem orchestrated via Docker Compose—will be deployed and configured by OneFirewall staff, equipped with a PoV License
- Verify network connectivity to ensure the solution can access and process the necessary traffic logs
- Perform final installation and connectivity checks to confirm the solution is fully operational within the infrastructure
Configuration
- Enable logging of all edge traffic to the OneFirewall VM
- Set up necessary permissions and integrations for comprehensive traffic analysis
Monitoring and Analysis
- OneFirewall begins real-time monitoring of network traffic
- Traffic is analyzed against the threat intelligence database to identify and classify potential threats
- Generate reports and alerts based on the analysis to provide insights into malicious activities
Evaluation
- Assess the volume and nature of detected threats
- Evaluate the responsiveness and accuracy of OneFirewall in identifying and mitigating potential cyber threats
- Gather feedback from network security personnel regarding the usability and effectiveness of the OneFirewall platform
Deliverables
Installation Report
Documenting the setup process and initial configuration of the OneFirewall VM
Traffic Analysis Report
Detailed insights into the detected threats, including types of attacks, sources, and frequency
Evaluation Report
Comprehensive assessment of OneFirewall's performance during the PoV, highlighting key findings and areas for improvement